
When it comes to connectivity options for IoT solutions, WiFi, LoRa and Cellular connectivity are typically the most discussed options. Though it undoubtedly depends on the Applications, traditional day-to-day WiFi is usually dismissed first–at least for any Applications other than consumer applications like the smart home. Though ideal for streaming video, for example, everyday WiFi is very impractical for anything out in the so-called customer field. That said, there is more to WiFi than what we use every day in a private or consumer setting.
Though they each have their pros and cons, WiFi, LoRa, and Cellular connectivity are all vulnerable to security risks and potentially serious consequences following a breach. Regardless of connectivity choice, focused attention should be given to considering robust IoT security features whatever the IoT solution.
An analysis of different short- and long-range wireless options based on their transmission characteristics when deploying an IoT solution at a customer site has provided us with several conclusions about connectivity. One conclusion is the general advantage of a cellular connection. But beyond the general benefits, what are the specific security benefits of cellular IoT connectivity compared to other connectivity options?
IoT Connectivity Options
Below we will review three of the most-used IoT connectivity options–WiFi, LoRa, and Cellular–and compare them from a security perspective. Specifically, we will compare the following four setups:
- Shared WiFi: when deploying the device at a remote site, it can be integrated into the customer’s WiFi network
- Dedicated WiFi: where WiFi routers are deployed together with the device(s)
- LoRa Network: we will consider shared LoRaWAN networks (like Loriot or The Things Network) where the Gateway, Network, Join and LoRaWAN application server is offered by a provider, as well as dedicated LoRaWAN networks where these components are deployed by the customer
- Cellular Connectivity: enables devices to be used at the edge, offering longer battery life and reliable connectivity
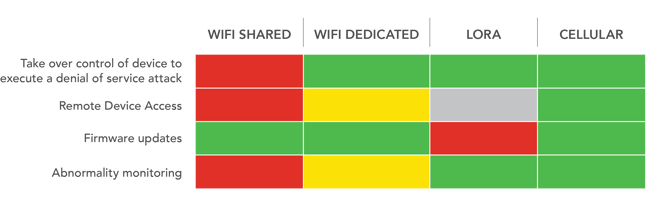
Comparison Based on Four Security Features
To begin, a quick snapshot below of how these four set-ups compare on four common security features:
Botnet Attack From a Compromised Device
There were 800 percent more Mirai attacks in the first half of 2019 compared to the first half of 2018. The Mirai malware has infected many IoT devices, creating a botnet that started distributed denial of service attacks on their victims. Worth noting (and perhaps unsurprising based on the above comparison chart) is that these IoT devices were mainly connected to the public internet or over shared WiFi and were able to reach any destination.
When choosing dedicated WiFi hardware, businesses should select routers with integrated firewalls that can be used to limit the number of IP addresses that the devices can reach, thus making it impossible for the device to attack another target or be commanded from a hacker’s control center.
LoRa devices cannot be directly reached and communicate with the Internet because they do not utilize the Internet protocol. LoRa devices can only talk to LoRaWAN applications to which they have been registered – and the management is done on the LoRa network server.
While there are reports of the danger of LoRa devices being able to execute DDoS attacks against other LoRaWAN devices or servers, these cases are due to poor implementation or addressed in future LoRaWAN specifications.
By using a cellular network firewall, IoT businesses can ensure that a device can only send data to its application target; thus, blocking all malicious traffic already on the network level.
Remote Device Access
Another vulnerability that the Mirai malware took advantage of is the unsecured remote device access of IoT devices on the public internet. Remote access is often necessary to do remote reconfigurations, retrieve data from the device and allow troubleshooting for support personnel. LoRaWAN does not have a concept for remote access and is therefore not judged on this feature.
Using standard WiFi routers, the IoT device gets a private address and is not visible from the public internet.
Remote device access is activated using port forwarding (and with DynamicDNS in case of dynamic IPs)–which Mirai has been using to infect even WiFi IoT devices within the private WiFi network.
With advanced WiFi infrastructure that allows setup of a virtual private network (VPN), remote device access can be secured – as only authenticated devices with the right VPN credentials will get access to the network. While this works with single, local deployments – managing multiple VPNs at different customer locations with the same private networks is challenging.
Cellular connectivity with private static IP addresses enables simple remote access via one virtual private network across all customer locations. The devices are not visible from the Internet and can be accessed by a VPN connection to the mobile network operator gateway.
Firmware Updates
Remote firmware updates are a critical part of keeping device security up to date. Security vulnerabilities can originate from customer-owned device firmware bugs, as well as from 3rd party libraries. Updating the device can be challenging; the remote update process must be guarded against attackers while also guaranteeing an easy roll-back in case of error.
Due to the downlink limitation of 10 messages per day, LoRa can only be used for updating very simple devices and even then, the update process can take days to weeks to complete. Initially, updates were only possible device by device, but multicast support for remote updates over LoRa has since been specified.
There are a wide range of solutions available for remotely updating firmware over Wi-Fi and cellular. Cloud platform providers like AWS, Azure and Google offer remote device management services, but there are also other providers like Balena or AV System.
Abnormality Monitoring
A central part in any security design is the ability to monitor for abnormalities. For all wireless connectivity technologies, the change of traffic log parameters can help to detect device tampering and serves as a safeguard against human error.
LoRaWan data is centrally managed within the application and network server – not only making payload data (e.g. the temperature measurement) available, but also important connectivity information like signal strength and packet loss.
Standard WiFi routers have a basic set of traffic logs that provide limited visibility. To effectively monitor abnormalities, the WiFi router not only needs to support detailed traffic information but also to centrally monitor and manage multiple customer sites.
With a cellular connectivity solution, detailed connectivity information, such as network signaling events and data volume, are available for all devices in real-time within the web-portal. This data can also be streamed to cloud platforms (AWS, Azure, Google Cloud) or third-party platforms (DataDog, DevicePilot) that already provide abnormality monitoring as a service.
Summary
As shown above, installing IoT devices using the customer’s WiFi infrastructure comes with several security risks. For this reason, it is advised to use one network for IoT devices and a separate network for normal operations, in order to safeguard both device types from each other. This way, IoT devices can’t impact normal devices, and outdated personal computers on shared LAN, for example, can’t serve as entry points for IoT devices.
LoRaWAN has very tight security concepts – coupling device to network and each application. It is best suited for low bandwidth applications, including in hard to reach locations, such as temperature sensors in a manufacturing setting. Often the LoRa gateways are connected via cellular connectivity to the public internet so data can be processed in a central place.
Dedicated WiFi infrastructure and cellular connectivity are the most-used wireless technologies for industrial IoT. By using a firewall, remote access, firmware updates, and monitoring, IoT businesses can benefit from a comprehensive security feature already on the network level.
For deployments at multiple customer sites and for mobile Applications, cellular connectivity not only provides seamless coverage but also makes it easier for an IoT service provider to manage the different installations. These are just two of numerous advantages of cellular connectivity over other options. Additional advantages are:
- Network coverage is available almost everywhere
- The device works immediately at the customer site
- No additional infrastructure and integration are required
- Low power technologies for pro-longed battery life (LTE-M/NB-IoT)
- Supports low and high transmission bandwidth in up- and downlink
The above advantages are quickly rendered useless in the event of poor security though. So, whatever connectivity option you decide is right for your IoT solution–make sure you take the recommended steps to robustly secure it.










 Latest IoT News
Latest IoT News









